Today Woo’s engineering team deployed an important update for WooCommerce. The update addresses a vulnerability that could allow bad actors to inject malicious content in the browser. The Woo team has also contacted WooCommerce merchants whose stores may be vulnerable.
This issue was limited to WooCommerce stores running the following WooCommerce versions that also had Order Attribute enabled, a feature that is enabled by default in WooCommerce:
| 8.8.0 | 8.8.1 | 8.8.2 | 8.8.3 |
| 8.8.4 | 8.9.0 | 8.9.1 | 8.9.2 |
If you are running WooCommerce 8.8.0 or later, we strongly recommend updating as soon as possible.
Actions you should take to ensure your store is updated
If you don’t have the right version installed already, you’ll need to update it manually.
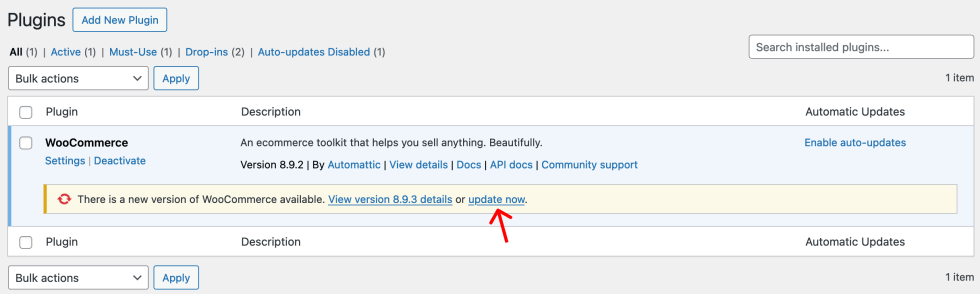
To update the extension:
- Log in to your store’s WP Admin dashboard and navigate to Plugins.
- Locate WooCommerce in your list of installed plugins and extensions. You should see an alert stating, « There is a new version of WooCommerce available. »
- Click the update now link displayed in this alert to update to version 8.9.3.
If you are unable to update WooCommerce immediately, you should disable Order Attribution. This vulnerability is only exploitable if Order Attribution is enabled.
You can read more about the update in this Woo Developer Advisory, including how to check your store’s version status.
What is the vulnerability?
This vulnerability could allow for cross-site scripting, a type of attack in which a bad actor manipulates a link to include malicious content (via code such as JavaScript) on a page. This could affect anyone who clicks on the link, including a customer, the merchant, or a store admin.
Has my store’s data been compromised?
We are not aware of any exploits of this vulnerability. The issue was originally found through Automattic’s proactive security research program with HackerOne. Our support teams have received no reports of it being exploited and our engineering team analyses did not reveal it had been exploited.
I use a version of WooCommerce older than 8.8.0; is my store impacted?
The vulnerability impacts any WooCommerce Shop running WooCommerce 8.8.0, 8.8.1, 8.8.2, 8.8.3, 8.8.4, 8.9.0, 8.9.1, 8.9.2, specifically if the store has Order Attribution enabled (this is enabled by default). If you are using an earlier stable, updated version of WooCommerce, your store is not affected.
How do I know if my store is safe?
If your store is running the latest, patched version of WooCommerce (8.9.3), it is safe.
What else can I do to keep my store secure?
We always encourage merchants to maintain high security standards. This includes the use of strong passwords, two-factor authentication, careful monitoring of transactions, and using the latest, secure version of WooCommerce (and any other extensions or plugins installed on your site). Read more about security best practices.
If you have further concerns or questions, our team of Happiness Engineers is on hand to help — please open a support ticket.
Special Thanks
We are grateful for the help of security researcher ecaron, who worked with us to uncover this vulnerability as part of Automattic’s HackerOne Bounty Program.
About


Please email the potential data that’s been compromised. This attack has compromised two of my sites repeatedly and I’ve had to contact my hosting company numerous times believing this issue was on their part. It’s great that the issue has been uncovered, but we want to know what next steps should be taken after updating WooCommerce.
Hi Richard – thanks for sharing this. Woo’s engineering team is taking a look at this topic now, and we’re hoping to share some general guidance for merchants and developers that can help ascertain whether stores may have been impacted by a vulnerability (examining logs, looking for specific activity patterns, etc).
As soon as we have some material, we’ll update this post and make sure to get it into our WooCommerce documentation and refer to it as a resource when these types of issues arise.
The team wanted to pass this information along as some good, general interim practices for any merchants who believe their shop may have been affected:
Most importantly, merchants should ensure they have upgraded WooCommerce to the latest release or the backport for your version.
There are a number of steps you can take to clean up any potentially compromised sessions:
* API Key Rotation: If you use API keys, we advise you to rotate these to prevent unauthorized access.
* User/Admin Account Review: Remove any legacy or unknown user/admin accounts to reduce the risk of unauthorized access.
* User Session Cleanups: Invalidate user sessions and prompt users to log in again as an added layer of security
Hi,
I updated to the lates version of Woocommerce 9.0.2 and I get this message « An important update is required for WooCommerce
An important security update for WooCommerce has been released. It is recommended that you update as quickly as possible. »
Than no updates are available into the updates page, or into the plugins’ list.
The problem is that I get a criticat error if I want to edit a order.
What’s going on?